Local Credential Store
Overview
Organizations without Active Directory often struggle to enforce identity-based web access due to the absence of centralized directory services. SafeSquid enables authentication via browser prompts by assigning usernames and passwords stored locally. This configuration eliminates LDAP dependency, simplifies access control, and enforces user-level policies using HTTP Basic Authentication integrated into SafeSquid’s credential manager.
Requirements Overview
User-Side Requirements
- Modern browser with HTTP Basic Authentication support.
- Pre-configured proxy in browser settings (manual or via PAC file).
SafeSquid-Side Preparation
- SafeSquid deployed and operational on internal network.
- Admin access to SafeSquid's configuration interface.
- "Enable Authentication" set in access profiles.
- Policy management interface available via HTTP/HTTPS.
Setup Browser Authentication
-
Ensure SafeSquid is Installed and Running
Access the SafeSquid configuration interface athttp://safesquid.cfg/through a browser using the SafeSquid proxy. -
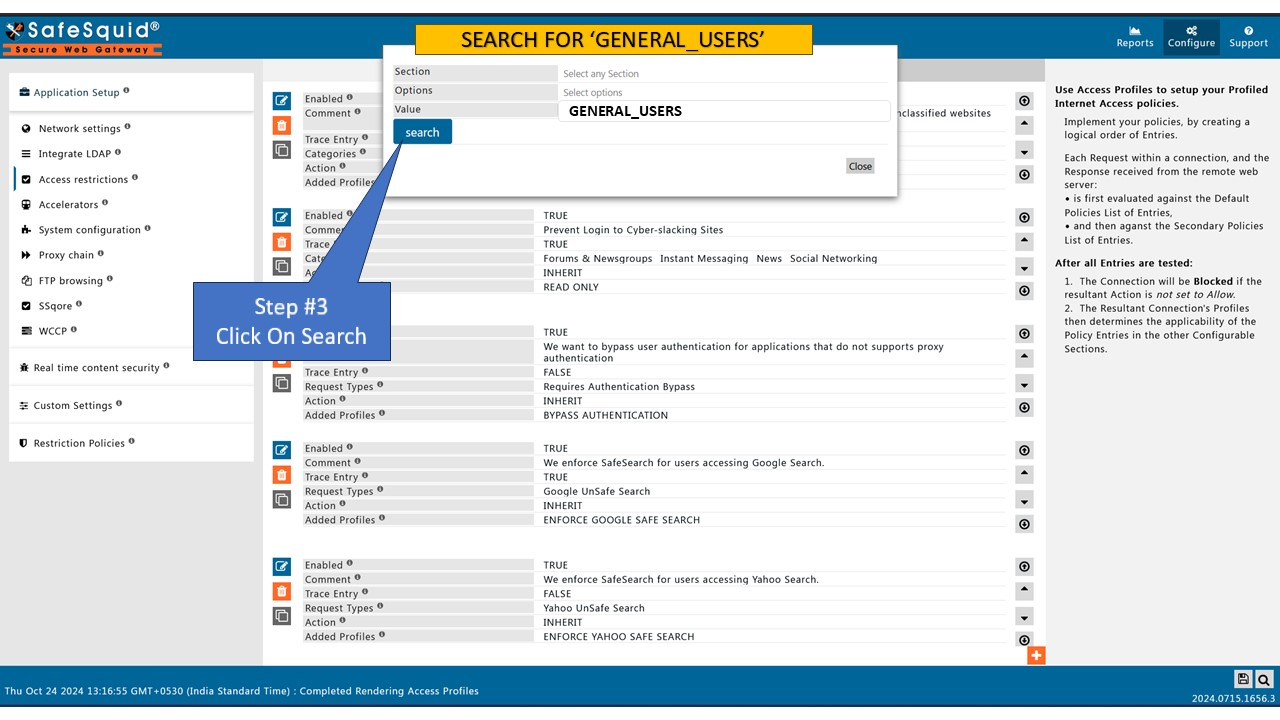
Navigate to Access Restrictions
From the left menu:Application Setup→Access Restrictions→Allow List.
Click the orange+icon to add a new entry.
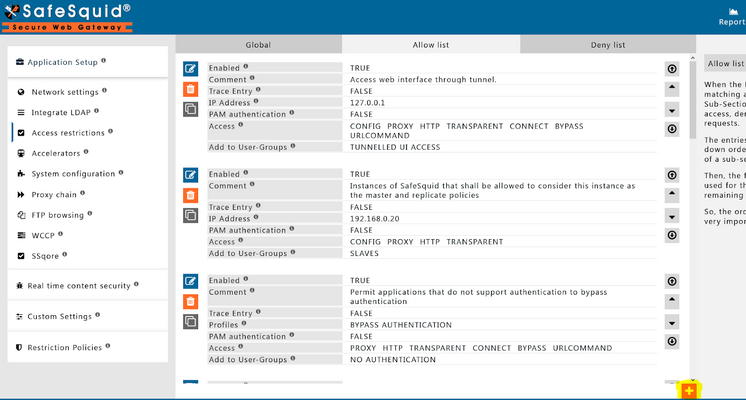
-
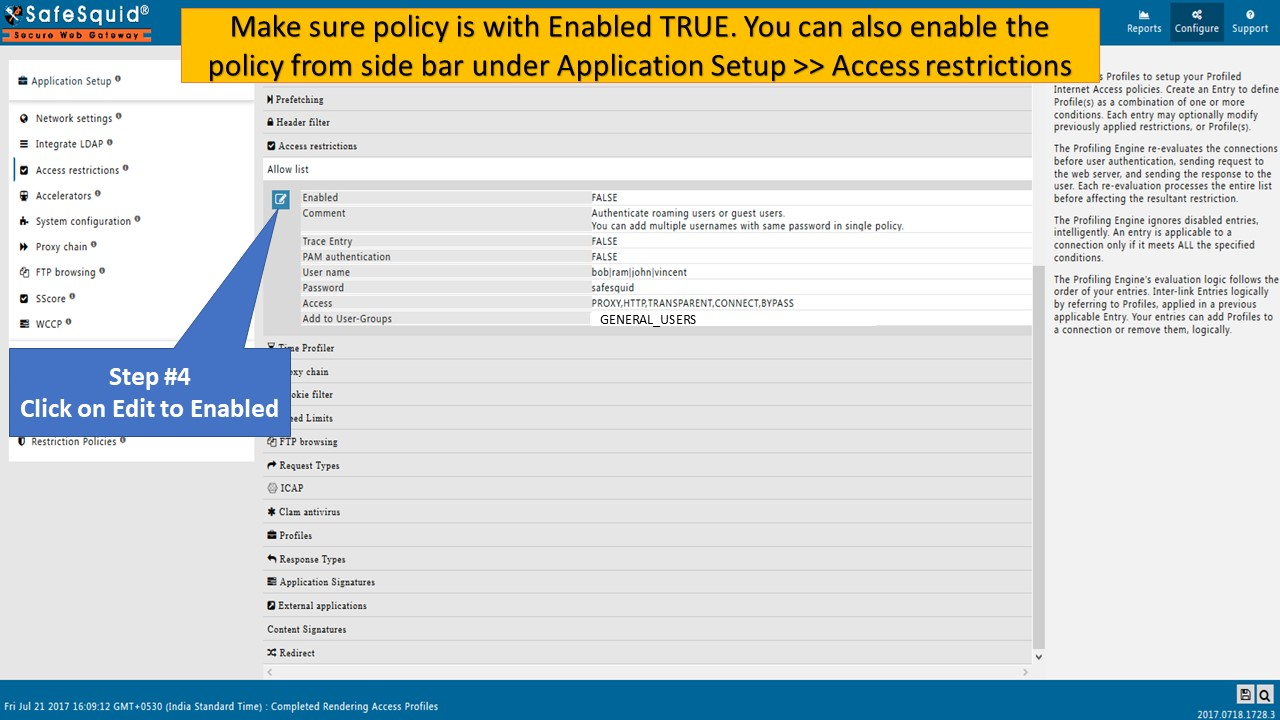
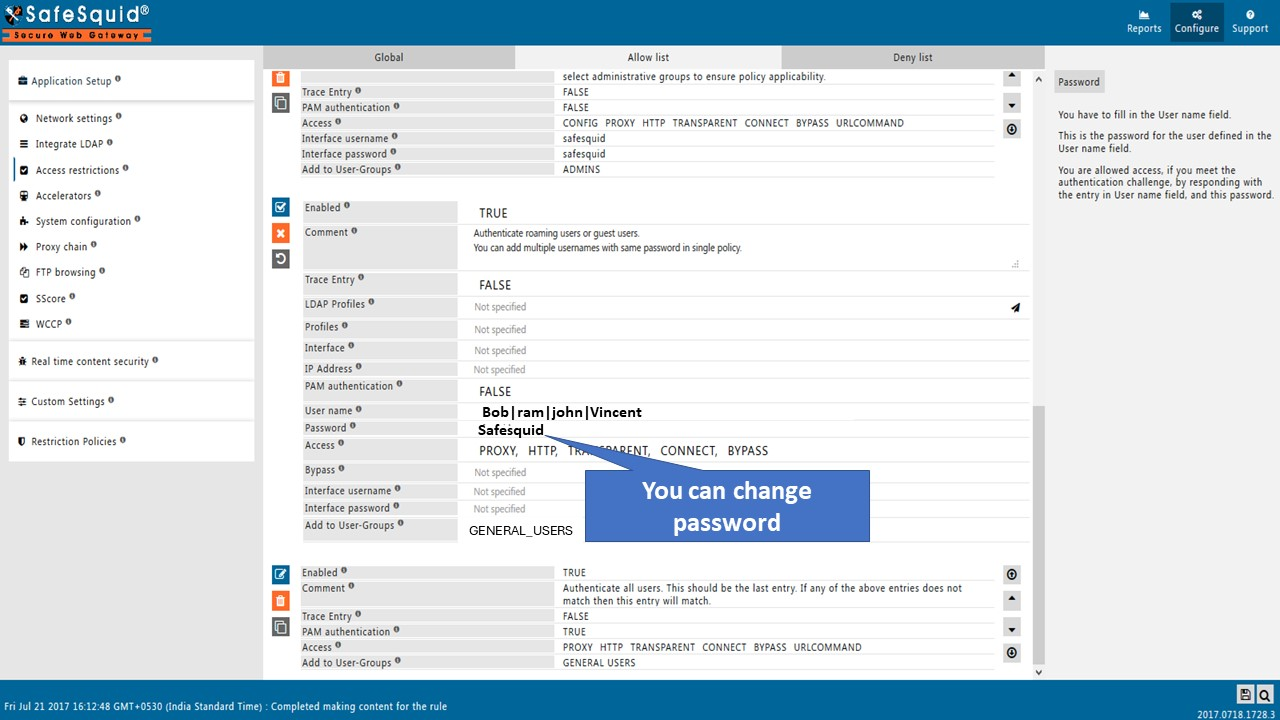
Disable PAM Authentication
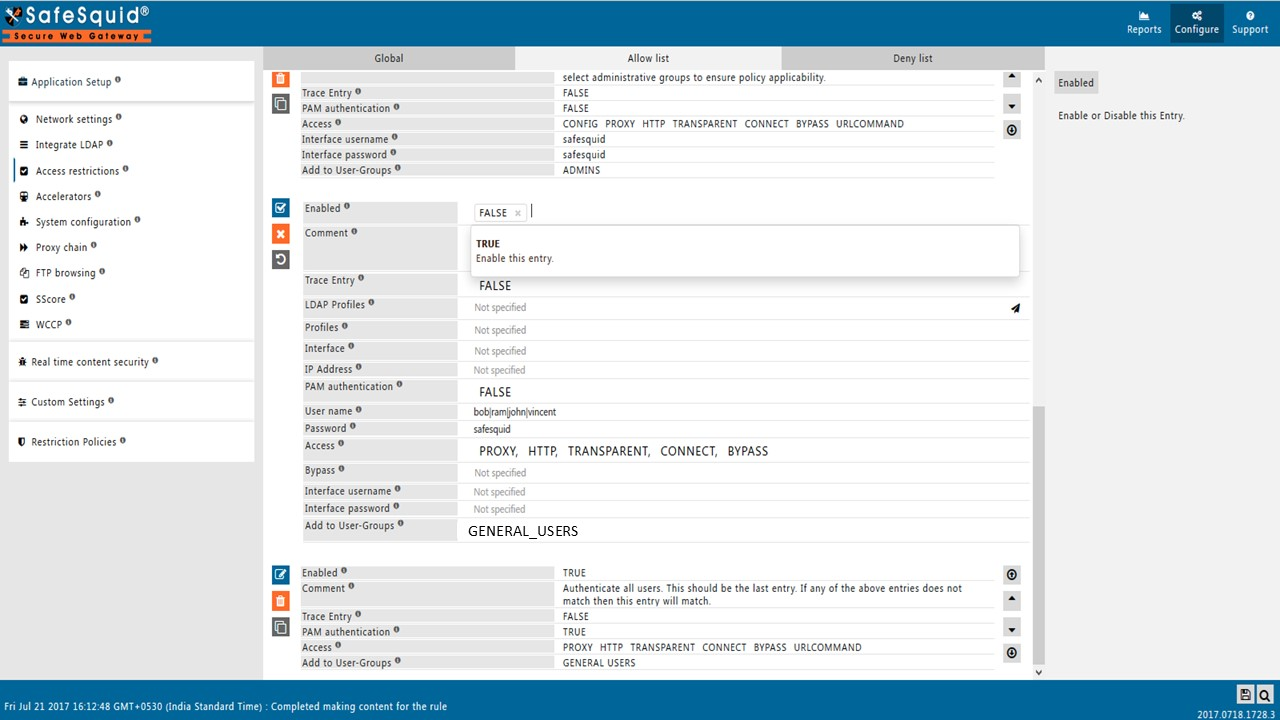
In the new rule window, setPAM AuthenticationtoFALSE.
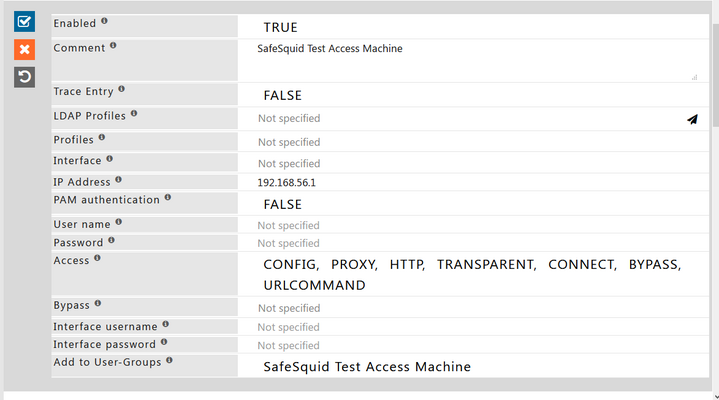
-
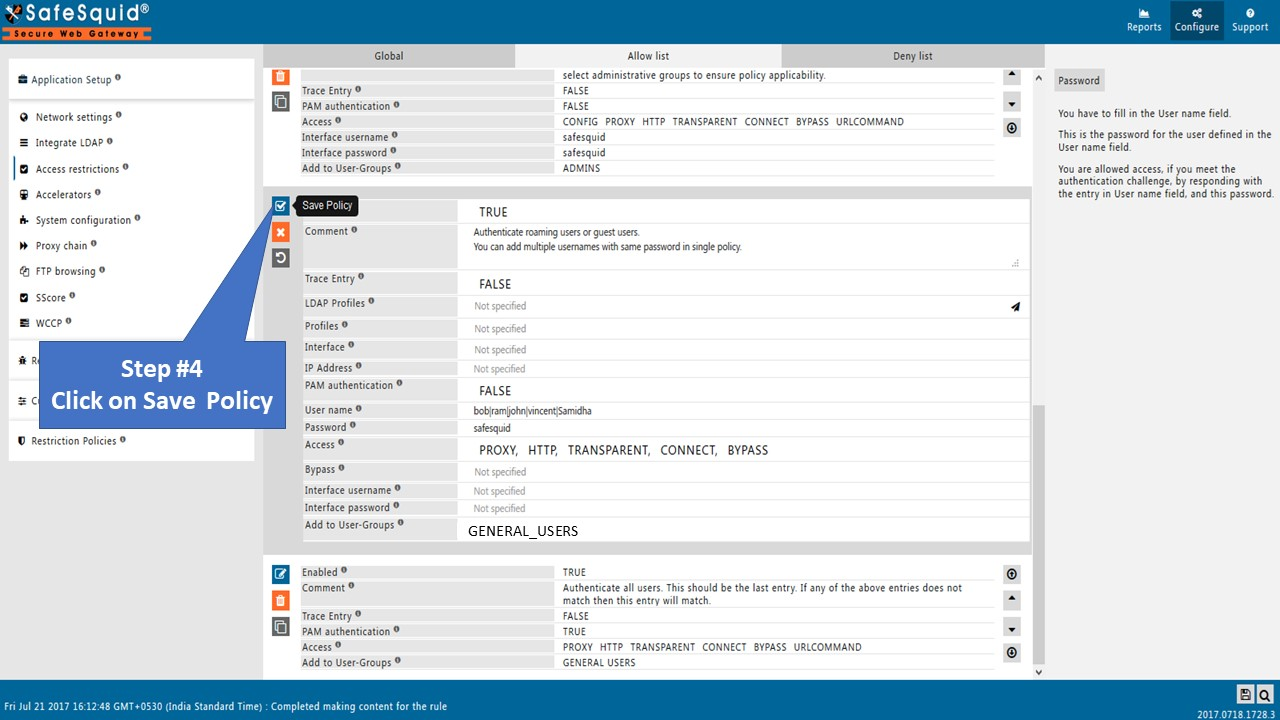
Save the Configuration
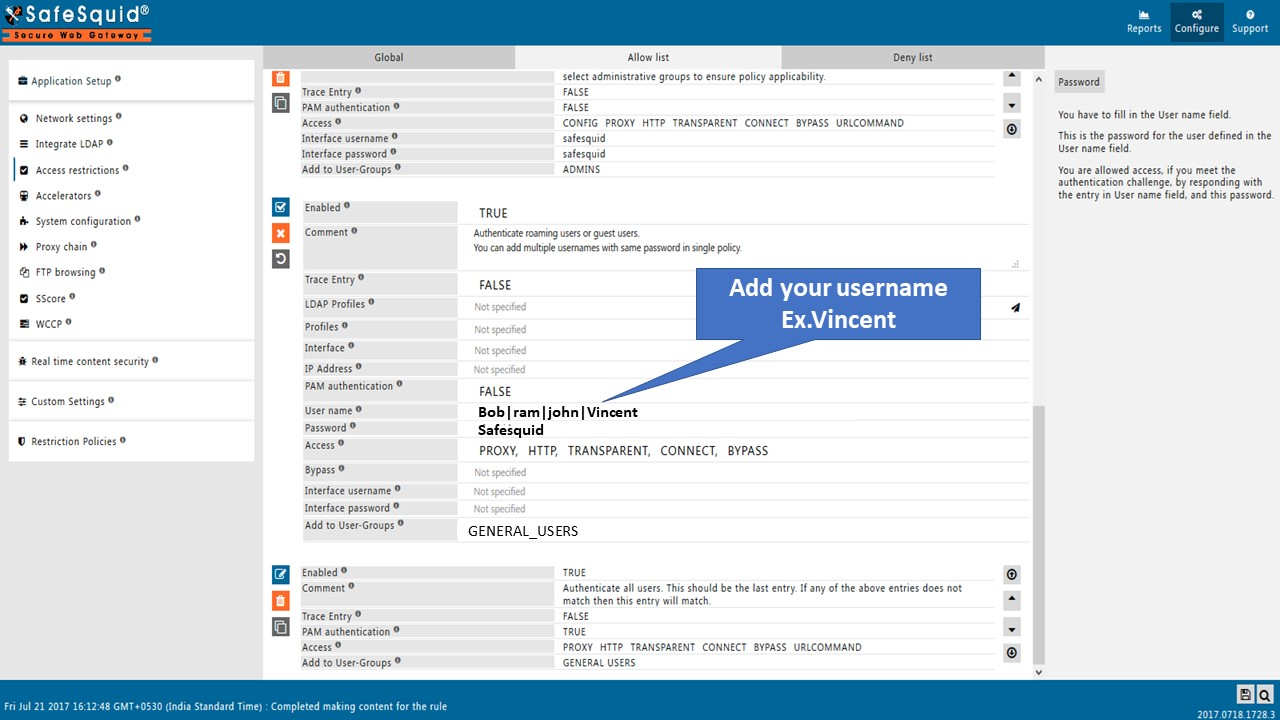
Click the checkmark to save the rule. A browser prompt will now appear asking for username and password when accessing the internet.
Add User
- From SafeSquid Interface
- From Linux Terminal
Instead of using the SafeSquid configuration interface, users can also be created directly on the Linux machine where SafeSquid is installed:
-
Create a New User
Run the following command in terminal:useradd name_of_the_user -
Set the Password
Assign a password using:passwd name_of_the_userIt will prompt to enter and confirm a new password.
Authentication Verification
- Attempt to browse any external site.
- Username/password prompt should appear.
- Enter credentials as configured.
- Access granted if authentication is successful.
Log Verification
Check identity.log or access.log for user authentication entries.
Issue Resolution Matrix
| Issue | Symptom | Likely Cause | Resolution |
|---|---|---|---|
| No login prompt | Direct access granted | Auth not enabled in access rule | Enable PAM to FALSE and add credentials |
| Login fails | Repeated prompts | Incorrect credentials or misconfigured rule | Verify username/password fields |
| Rule not enforced | Open access for all | IP mismatch or missing fields | Ensure IP and access permissions are accurate |